This tutorial explains how to lock down the EdgeRouter DNS configuration and force all LAN client requests to a DNS security & content filtering service to block ransomware, malware, botnets, phishing domains and enforce content filters for inappropriate websites.
DNS Security & Content Filtering Benefits
DNS is used by ransomware, exploit kits and botnets to find the IP address of the Command & Control (C&C or C2) servers to receive instructions and upload stolen data. Phishing uses DNS to resolve the IP address of a look-alike website to steal your login credentials. Content filtering blocks web sites that may be inappropriate for school, work or might be illegal such as adult content, gambling, piracy, etc.
Most users don’t realize their home router automatically obtains the DNS servers from their Internet Service Provider (ISP) which only provides basic DNS security in the spirit of an open Internet. Savvy users may manually configure the router to use Google or OpenDNS which do a good job blocking malicious sites and/or provide content filtering.
Enterprise DNS services – meaning a paid subscription is required – are focused on the business market and provide more security, finer control, analytics, notifications and reporting. Notifications are valuable Indicators of Compromise because it can tell you which device in your network – including the MAC address – is at risk so you can take corrective actions. Examples of enterprise DNS security services in alphabetical order are:
- DNSFilter
- Cisco Umbrella
- Cyren
- Neustar – (also see the free small business service)
- Nominum
- Verisign
A review of personal and enterprise DNS services is outside the scope of this article.
Project series index:
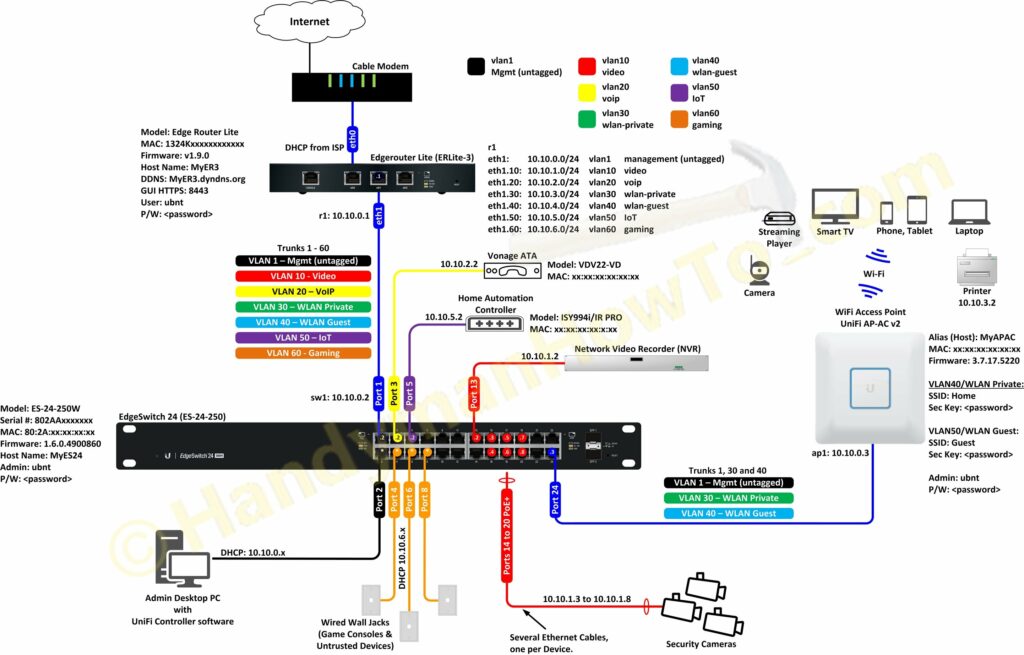
- Ubiquiti EdgeRouter Lite SOHO Network Design
- Ubiquiti EdgeRouter Lite SOHO Network Configuration
- EdgeRouter Lite SOHO Network Firewall Rules
- Ubiquiti EdgeRouter DNS Security & Content Filtering – Block Ransomware, Botnets, Phishing and Inappropriate Content (you are here)
- Ubiquiti EdgeRouter: How to Enforce Different DNS Servers per VLAN
- Ubiquiti EdgeRouter OpenVPN Server-Client Configuration Tutorial
- EdgeRouter OpenVPN: Create Public Key Infrastructure with Easy-RSA
- EdgeRouter OpenVPN Server – Client Mode Configuration Steps
- OpenVPN iPhone Client Configuration Steps
- OpenVPN Windows 10 Client Configuration Steps
Ubiquiti EdgeRouter DNS Security & Content Filtering – Block Ransomware, Botnets, Phishing and Inappropriate Content
The following EdgeRouter DNS configuration lock down is applicable to any DNS service; just specify the DNS server IP addresses of your choice.
The EdgeRouter Lite is configured as the DNS and DHCP server for my Small Office/Home Office (SOHO) network. Well behaved LAN clients are automatically configured via DHCP with the EdgeRouter DNS IP address of 10.10.0.1:
EdgeRouter DNS Destination NAT (DNAT) Rule
A LAN to WAN Destination NAT (DNAT) rule is configured to rewrite any rogue DNS queries to my preferred DNS server IP addresses, represented by aaa.bbb.ccc.ddd and eee.fff.ggg.hhh:
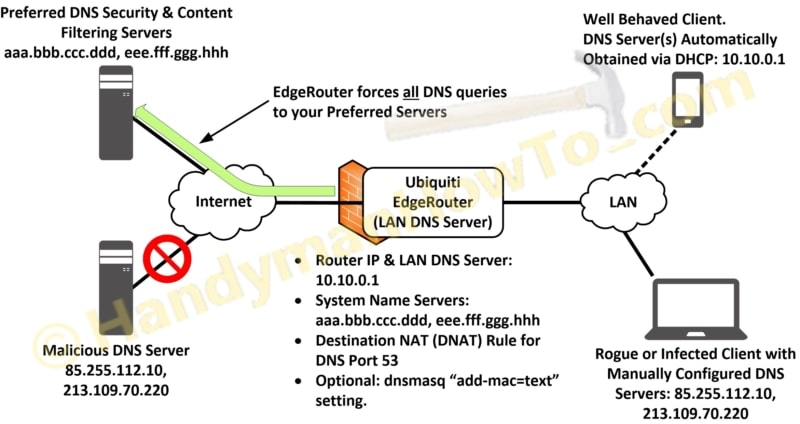
Suppose a LAN client is infected with malware or the user hard coded something other than my preferred DNS servers. The EdgeRouter DNAT rule will translate the rogue DNS server IP address to the EdgeRouter IP 10.10.0.1. The EdgeRouter then forwards the DNS query to the preferred DNS servers at aaa.bbb.ccc.ddd or eee.fff.ggg.hhh.
The DNS DNAT rule CLI commands are:
set service nat rule 10 description 'Policy DNAT: Force LAN DNS Requests to Router' set service nat rule 10 inbound-interface eth1 set service nat rule 10 destination address !10.10.0.1 set service nat rule 10 destination port 53 set service nat rule 10 inside-address address 10.10.0.1 set service nat rule 10 protocol tcp_udp set service nat rule 10 type destination set service nat rule 10 log enable
and in pretty print mode:
ubnt@ubnt# show service nat rule 10
rule 10 {
description "Policy DNAT: Force LAN DNS Requests to Router"
destination {
address !10.10.0.1
port 53
}
inbound-interface eth1
inside-address {
address 10.10.0.1
}
log enable
protocol tcp_udp
type destination
}
The DNAT rule operates as follows:
- Eth1 is the LAN interface.
- Match inbound traffic to port 53 (DNS) that is not destined for the EdgeRouter via the ! (not) operator: !10.10.0.1
- inside-address translates the source IP address to the router IP 10.10.0.1
- Enable logging so I can investigate rogue devices by checking /var/log/messages.
Use “log disable” if you don’t want logging. - DNS uses TCP and UDP protocols, so match both.
Change the NAT Rule # to something that doesn’t conflict with your existing rules and the router IP address to match yours.
Additional EdgeRouter DNS and DCHP Configuration Requirements
The following dependencies may already be implemented in your basic router configuration and included here for completeness.
The EdgeRouter Internet DNS name servers configuration commands are:
set system name-server aaa.bbb.ccc.ddd <-- put the real DNS server IP here set system name-server eee.fff.ggg.hhh <-- put the real DNS server IP here
Repeat the above command if you have additional DNS server IPs.
The “no-update” command is needed to prevent the EdgeRouter from adding my ISPs DNS servers to the list:
set interfaces ethernet eth0 dhcp-options name-server no-update
The EdgeRouter must forward DNS queries from the LAN to the WAN otherwise the client queries will fail:
set service dns forwarding listen-on eth1
If Eth2 is serving another LAN network configuring forward for it, too.
I have six VLANs so forwarding must be configured for those. Change the following interfaces to match yours. Skip these commands if you don’t have VLANs:
set service dns forwarding listen-on eth1.10 set service dns forwarding listen-on eth1.20 set service dns forwarding listen-on eth1.30 set service dns forwarding listen-on eth1.40 set service dns forwarding listen-on eth1.50 set service dns forwarding listen-on eth1.60
Destination NAT (DNAT) Rule Testing
I hard coded my Windows PC to use Google DNS servers to simulate a rogue client then opened a web browser and surfed the web while monitoring the NAT translations from the EdgeRouter CLI. Google DNS (8.8.8.8 and 8.8.4.4) queries are remapped to the EdgeRouter IP at 10.10.0.1:
ubnt@ubnt:~$ show nat translations destination monitor Type control-C to quit Pre-NAT Post-NAT Type Prot Timeout Type 8.8.8.8 10.10.0.1 dnat udp 30 new 8.8.8.8 10.10.0.1 dnat udp 30 update 8.8.8.8 10.10.0.1 dnat udp 30 new 8.8.8.8 10.10.0.1 dnat udp 30 update 8.8.8.8 10.10.0.1 dnat udp 30 new 8.8.8.8 10.10.0.1 dnat udp 30 update 8.8.8.8 10.10.0.1 dnat udp 30 new 8.8.4.4 10.10.0.1 dnat udp 30 new 8.8.8.8 10.10.0.1 dnat udp 30 update 8.8.4.4 10.10.0.1 dnat udp 30 update 8.8.8.8 10.10.0.1 dnat udp destroy 8.8.4.4 10.10.0.1 dnat udp destroy 8.8.8.8 10.10.0.1 dnat udp destroy
Checking the log shows the DNAT rule firing and the MAC address of the offending client:
ubnt@ubnt:~$ tail -n 100 /var/log/messages [NAT-10-DNAT] IN=eth1 OUT= MAC=dc:**:**:........:**:00 SRC=10.10.0.38 DST=8.8.8.8 LEN=69 TOS=0x00 PREC=0x00 TTL=128 ID=23998 PROTO=UDP SPT=58437 DPT=53 LEN=49 [NAT-10-DNAT] IN=eth1 OUT= MAC=dc:**:**:........:**:00 SRC=10.10.0.38 DST=8.8.4.4 LEN=66 TOS=0x00 PREC=0x00 TTL=128 ID=20109 PROTO=UDP SPT=49378 DPT=53 LEN=46
Summary statistics show the DNAT Rule 10 was triggered 318 times:
ubnt@ubnt:~$ show nat statistics rule count type IN OUT description ---- ---------- ---- -------- -------- ----------- 10 318 DST eth1 - Policy DNAT: Force LAN DNS Requests to Router 5010 190607 MASQ - eth0 masquerade for WAN
Dnsmasq: add-mac option
Enterprise DNS security services can optionally track and report the device MAC address that made a DNS query. That way the service can report the which device may be infected with ransomware, malware or attempted to reach a blocked URL. DNS security services provide an admin configuration page where you can enter known MAC addresses with user-friendly names like “Ubuntu Server 10” or “Bob’s iPhone”.
dnsmasq is a standard component of the EdgeRouter environment and the daemon is already running. The dnsmasq “add-mac” configuration option to “Add requestor’s MAC address to forwarded DNS queries” will include the LAN device MAC address in the query.
As of this writing I’m running the latest firmware v1.9.1.1 on my EdgeRouter Lite which includes dnsmasq v2.76:
ubnt@ubnt:~$ /usr/sbin/dnsmasq -v Dnsmasq version 2.76-1-ubnt2 Copyright (c) 2000-2016 Simon Kelley Compile time options: IPv6 GNU-getopt DBus i18n IDN DHCP DHCPv6 no-Lua TFTP conntrack ipset auth DNSSEC loop-detect inotify
To view the dnsmasq config file:
ubnt@ubnt:~$ cat /etc/dnsmasq.conf # # autogenerated by vyatta-dns-forwarding.pl on Mon Jun 19 21:00:40 EDT 2017 # log-facility=/var/log/dnsmasq.log interface=eth1 interface=eth2 interface=eth1.10 interface=eth1.20 interface=eth1.30 interface=eth1.40 interface=eth1.50 interface=eth1.60 interface=vtun0 cache-size=150
Because the dnsmasq.conf file is regenerated (overwritten) when DNS changes are made or firmware is upgraded you shouldn’t edit the dnsmasq.conf file. The best way to configure the “add-mac” option is via the EdgeRouter CLI in configuration mode:
set service dns forwarding options add-mac=text
Because the “add-mac” option is now part of the router config it will survive DNS changes & firmware upgrades:
ubnt@ubnt:~$ cat /etc/dnsmasq.conf
#
# autogenerated by vyatta-dns-forwarding.pl on Fri Jun 23 13:06:09 EDT 2017
#
log-facility=/var/log/dnsmasq.log
interface=eth1
interface=eth2
interface=eth1.10
interface=eth1.20
interface=eth1.30
interface=eth1.40
interface=eth1.50
interface=eth1.60
interface=vtun0
cache-size=150
add-mac=text
The offending LAN device MAC address now appears in the DNS security service notifications and reports.
DNS Lock Down Circumvention
Locking down the router DNS configuration as shown here will stop most but not all attempts to get around DNS security firewalls and content filtering. A user might evade the EdgeRouter DNS DNAT rule with an encrypted VPN tunnel, an app using a DNS over HTTPS API or DNScrypt all of which use port 443 instead of port 53. See Definitive Guide to Content Filtering Circumvention: And Lessons Learned in Prevention for more information.
Also see EdgeRouter Lite SOHO Network Firewall Rules for hardening and Ubiquiti EdgeRouter OpenVPN Server-Client Configuration Tutorial for secure remote access.
A follow-up to this tutorial is: Ubiquiti EdgeRouter: How to Enforce Different DNS Servers per VLAN.
Thanks for reading,
Bob