How to configure OpenVPN in Server/Client mode on a Ubiquiti EdgeRouter Lite for secure remote access from multiple clients to a small office/home office (SOHO) network:
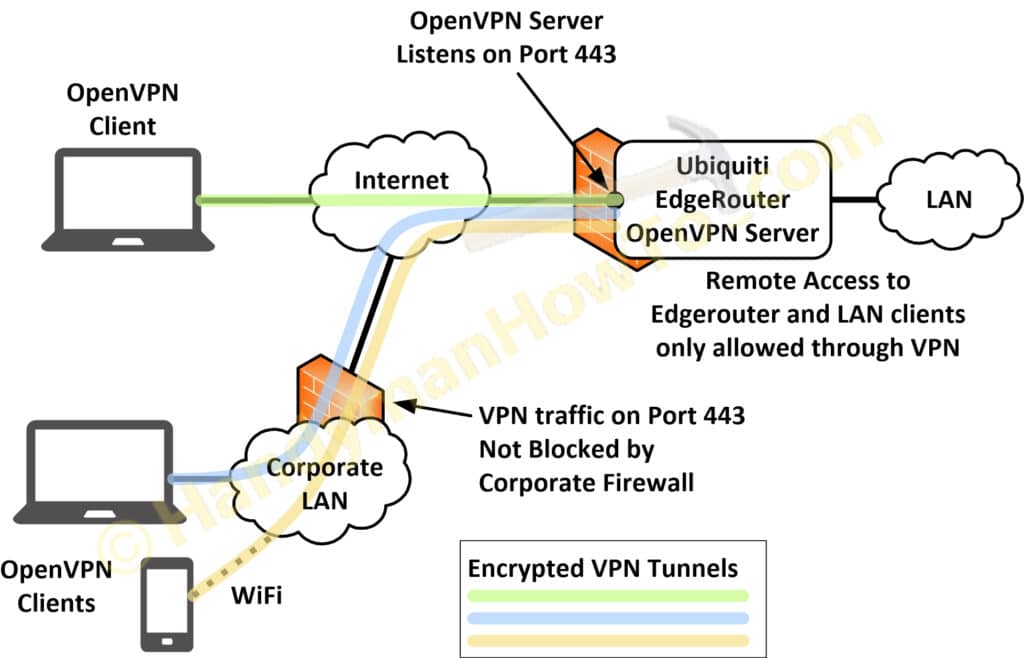
The EdgeRouter OpenVPN server listens on port 443 to pass through corporate firewalls that often block other TCP/IP ports. Port 443 is allowed on most firewalls because it’s used for HTTPS (HTTP over TLS/SSL) and the firewall can’t tell the difference between encrypted HTTPS and OpenVPN network traffic.
Port Forwarding is not enabled and I only allow OpenVPN connections to my home network. See VPN vs Port Forwarding (.pdf) by Luxul for details.
Project series index:
- Ubiquiti EdgeRouter Lite SOHO Network Design
- Ubiquiti EdgeRouter Lite SOHO Network Configuration
- EdgeRouter Lite SOHO Network Firewall Rules
- Ubiquiti EdgeRouter DNS Security & Content Filtering – Block Ransomware, Botnets, Phishing and Inappropriate Content
- Ubiquiti EdgeRouter: How to Enforce Different DNS Servers per VLAN
- Ubiquiti EdgeRouter OpenVPN Server-Client Configuration Tutorial (you are here)
- EdgeRouter OpenVPN: Create Public Key Infrastructure with Easy-RSA
- EdgeRouter OpenVPN Server – Client Mode Configuration Steps
- OpenVPN iPhone Client Configuration Steps
- OpenVPN Windows 10 Client Configuration Steps
Remote Access vs Site-to-Site vs Private Internet Access VPNs
There are several types of VPNs to solve various privacy and connectivity requirements:
-
Remote Access VPN
Provides remote connectivity to a LAN network from one or more clients as illustrated in the above diagram.
A client (smart phone, PC, teleworker, etc.) connects to an OpenVPN server (e.g. EdgeRouter). The VPN client behaves like a local user and can access network applications, printers and servers. Network administrators also use VPNs to manage the router, switches and servers. This is the way big companies do it and the subject of this tutorial. -
Site-to-Site VPN
A site-to-site VPN transparently links two remote networks through a secure connection over the Internet. This is useful when a company has two offices (each with a router & LAN) and needs to route traffic traffic between the two. The advantage is it only involves configuring the routers and is transparent (i.e. no changes) to the local servers and clients. -
Private Internet Access (PIA) VPN
PIA‘s are a means for anonymous Internet access to avoid eavesdropping by your Internet Service Provider (ISP) or to make it appear that your Internet connection (IP address) originates in a different country to access services that may be blocked in foreign countries.- A non-anonymous PIA-like configuration is supported by the Viscosity OpenVPN PC/MAC client to force all web browser traffic through the EdgeRouter and it’s Internet connection.
Ubiquiti EdgeRouter OpenVPN Server-Client Configuration Tutorial & Setup
This tutorial was extensively revised on April 7, 2018:
- Fixed iOS OpenVPN Connect 1.2.9 problems.
MD5 signed certificates will no be supported at the end of April 2018 and resolved “CORE_ERROR mbed TLS error parsing config private key PK” after creating a new private key. - EdgeRouter OpenVPN configuration updates.
- Easy-RSA 2.0 updates: openssl-1.0.0.cnf and procedure changes.
Platform Environment
The Public Key Infrastructure (PKI) and OpenVPN solution was built using the following software versions:
-
EdgeMAX EdgeRouter software version v1.10.1
- OpenVPN 2.3.2 mips-unknown-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [eurephia] [MH] [IPv6] built on Jan 25 2018
- OpenSSL 1.0.1e 11 Feb 2013, which is bundled with the EdgeRouter operating system.
- Windows 10
- OpenVPN 2.4.5 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Mar 1 2018
- OpenSSL 1.1.0f 25 May 2017, which is bundled with OpenVPN
- Viscosity 1.7.8 (1560) Windows client.
- Apple iPhone running iOS 11.3
- OpenVPN Connect 1.2.9 build 0 (iOS 64-bit). Available on iTunes.
Note the EdgeRouter OpenVPN and OpenSSL versions are much older compared to the Windows 10 and Apple iOS clients. The outdated EdgeRouter OpenVPN v2.3.2 doesn’t support TLS v1.2 and stronger ciphers such as TLS-DHE-RSA-WITH-AES-256-CBC-SHA256 nor the Elliptic Curve suites.
Public Key Infrastructure
Configuring OpenVPN is a bit complex but I’ve provided diagrams and a complete working PKI that should make it a straightforward exercise. This tutorial only assumes your EdgeRouter is up & running and you want to enable OpenVPN in server/client mode.
The Public Key Infrastructure (PKI) consisting of the root Certificate Authority (CA), Server & Client Certificates and Private Encryption Keys will be created on a Windows 10 desktop PC using the OpenVPN easy-rsa scripts included with OpenVPN. The certificates, keys and OpenVPN (.ovpn) client Profiles will be installed on the EdgeRouter, iPhone and Windows 10 laptop:
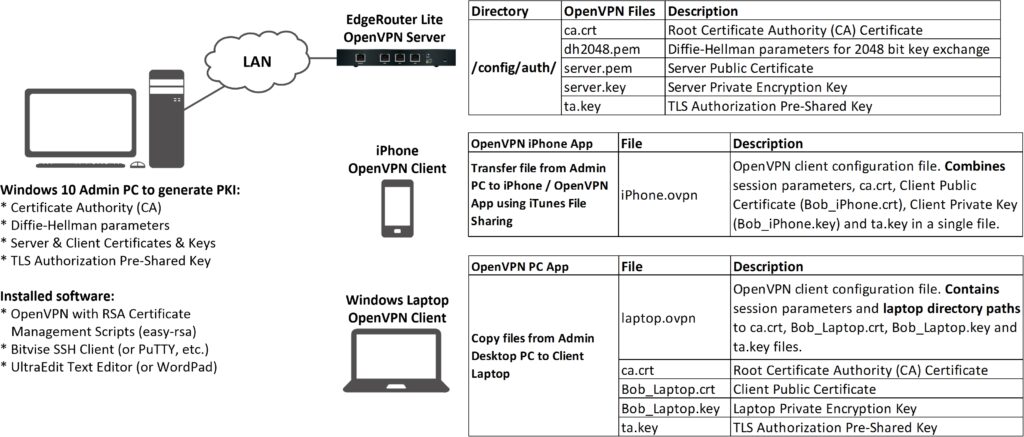
Creating the PKI and related items is faster, more convenient and secure on the Windows PC versus directly on the EdgeRouter. You also have to use Apple iTunes on the PC to sync the iPhone OpenVPN client configuration file.
Windows 10 Admin PC Software Apps
The software applications installed on the Windows 10 Admin PC are:
-
OpenVPN – Installer for Windows. It’s free.
The “easy-rsa 2” scripts are bundled with the Windows installer. - bitvise SSH & SFTP client for convenient GUI access from the Windows Admin PC to the EdgeRouter. Also free.
- UltraEdit is my favorite text editor but any text editor will do.
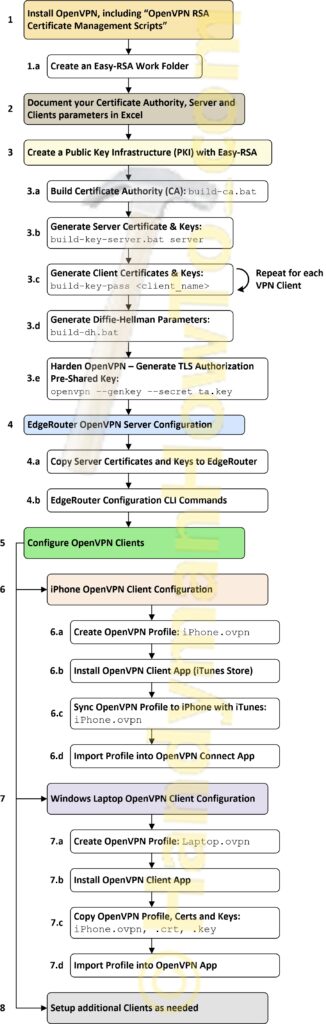
OpenVPN Configuration Process Diagram – EdgeRouter Server and Clients
The following OpenVPN configuration process diagram outlines the major steps to setup OpenVPN on the EdgeRouter, laptop and iPhone:
The following instructions covers steps 1, 1.a and 2 in this except from the above master process diagram:
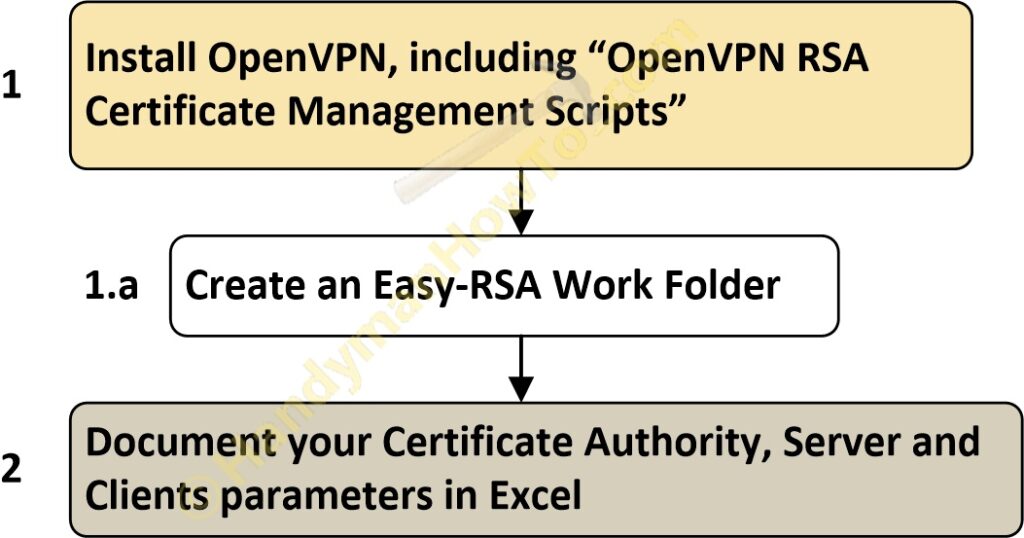
1. Install OpenVPN
Download OpenVPN for Windows and run the installer. Be sure to select “OpenVPN RSA Certificate Management Scripts” which will also install the easy-rsa scripts:
Choose the default installation folder, C:Program FilesOpenVPN:
After the installer is finished, there’s an easy-rsa folder in C:Program FilesOpenVPN:
1.a Create an Easy-RSA Work Folder
Doing work in C:Program Files isn’t a best practice. Create a new folder C:OpenVPN-Server-Client-Build for where the Certificate Authority, certificates and keys will be generated. I created a new folder in the C: root directory to keep the directory paths short for this tutorial. A better place would be in your Windows Documents folder.
Copy C:Program FilesOpenVPNeasy-rsa folder and contents to C:OpenVPN-Server-Client-Build. Screen grab after copying the folder:
2. Document your Certificate Authority (CA), Server and Clients parameters in Excel
Decide now what to name your CA, organization, Common Names, Private Key (PEM) Passphrases, etc. because these values will used by the easy-rsa scripts. Since this is a home network instead of a company or institution with a real domain name (i.e. example.com) you’ll need to invent meaningful names. The most important items are the Common Names which must be unique within your Certificate Authority.
Create an Excel Worksheet or text file to document your CA. This document is highly confidential because it contains your client Private Key (PEM) Passphrases. I keep my sensitive files in an encrypted Apricorn Aegis Secure Key for on-the-road access. The Excel worksheet is:
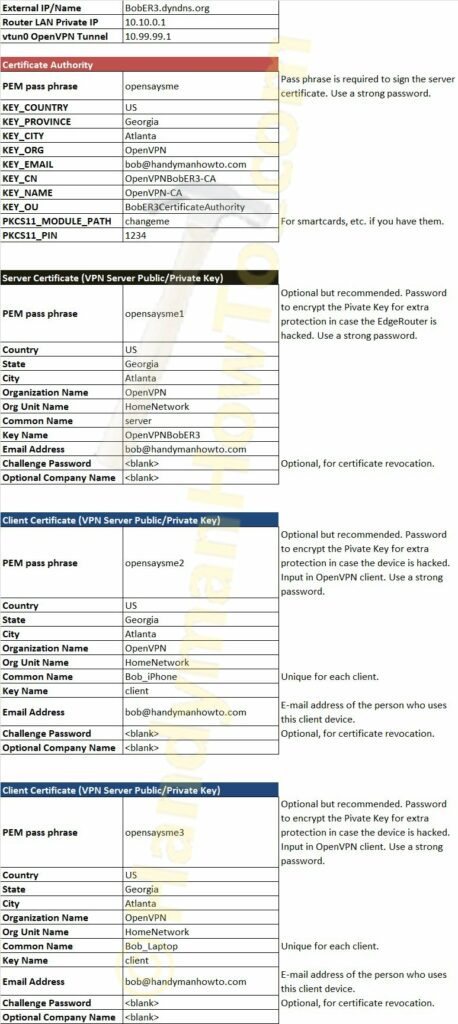
The following parameters are the same as in the above Excel worksheet.
The CA parameters in this example are:
| Certificate Authority | |
|---|---|
| PEM pass phrase | opensaysme |
| KEY_COUNTRY | US |
| KEY_PROVINCE | Georgia |
| KEY_CITY | Atlanta |
| KEY_ORG | OpenVPN |
| KEY_EMAIL | bob@handymanhowto.com |
| KEY_CN | OpenVPNBobER3-CA |
| KEY_NAME | OpenVPN-CA |
| KEY_OU | BobER3CertificateAuthority |
| PKCS11_MODULE_PATH | changeme |
| PKCS11_PIN | 1234 |
The EdgeRouter Server Certificate parameters are:
| Server Certificate (VPN Server Public/Private Key) | |
| PEM pass phrase | opensaysme1 |
| Country | US |
| State | Georgia |
| City | Atlanta |
| Organization Name | OpenVPN |
| Org Unit Name | HomeNetwork |
| Common Name | server |
| Key Name | OpenVPNBobER3 |
| Email Address | bob@handymanhowto.com |
| Challenge Password | <blank> |
| Optional Company Name | <blank> |
and the iPhone client:
| Client Certificates (VPN Server Public/Private Key) | |
| PEM pass phrase | opensaysme2 |
| Country | US |
| State | Georgia |
| City | Atlanta |
| Organization Name | OpenVPN |
| Org Unit Name | HomeNetwork |
| Common Name | Bob_iPhone |
| Key Name | client |
| Email Address | bob@handymanhowto.com |
| Challenge Password | <blank> |
| Optional Company Name | <blank> |
The laptop client certificate is very similar to the iPhone table above except the “Common Name” is Bob_Laptop and the PEM Passphrase is “opensaysme3”.
The PEM Passphrase is optional but a recommended extra layer of security to encrypt the OpenVPN client Private Key. It should be strong password and not “opensaysme” in this example! The passphrase is input when the OpenVPN client is run. It’s an extra safeguard in case your laptop files are stolen and to prevent someone from connecting to your OpenVPN if they have your iPhone or laptop.
This tutorial is continued in EdgeRouter OpenVPN: Create a Public Key Infrastructure with Easy-RSA.
Thanks,
Bob